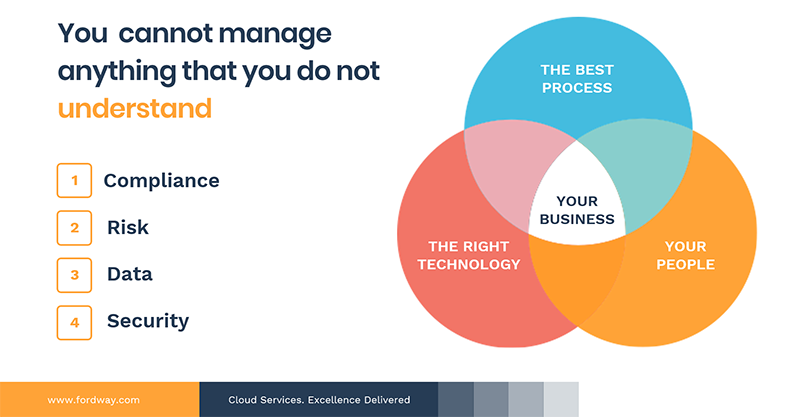
What are the key technologies -that can protect your business from cyber-attacks?
Most businesses would look for technologies such as threat detection, anti-malware, firewalls, and antivirus software. The choice comes down to how often your systems are patched, or what policies and procedures are in place.